|
||||
|
||||
|

|
|
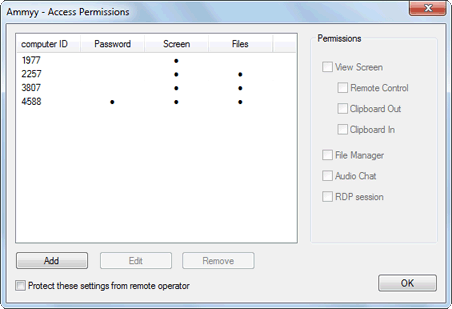
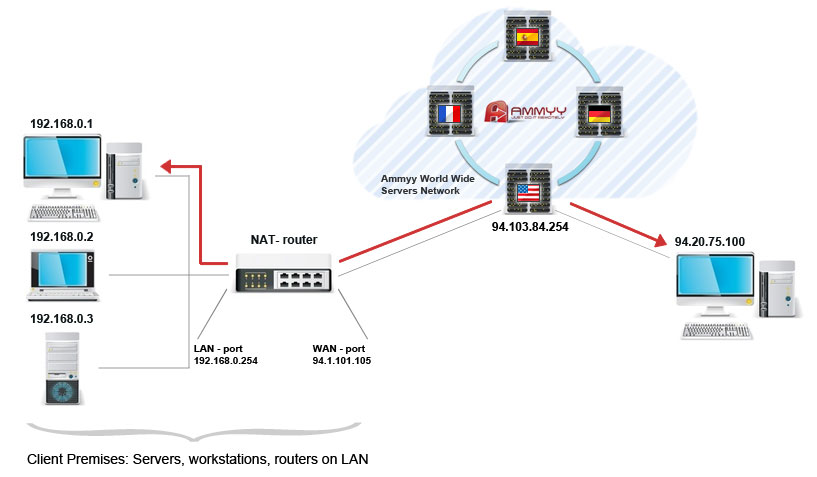
Ammyy Admin Security White PaperAmmyy Admin provides strong end-to-end solutions to data security that make data confidentiality safe. Scope and audience This guide is for Ammyy Inc. customers and those who need to understand how Ammyy Admin impacts information security risk and compliance in their environment. This document solely addresses the Ammyy Admin product. Introduction Ammyy Admin is multitask software that allows IT and support professionals to provide remote support to computers and servers as well as to organize on-line meetings for collaborative or educational purposes. Ammyy Admin allows a support representative to view and control an end user's Windows based PC remotely. Definitions Operator - a PC from which a support provider representative connects to a remote PC of a client and control it in order to deliver tech support or for other purposes. Authentication Hardware ID Ammyy Admin generates and binds unique ID to a PC on which it's run. This ID is based on PC hardware configuration and is generated only once what makes this key a unique PC identifier which is impossible to imitate or fake. Connection accept Ammyy Admin supports multilevel authentication system which provides a secure access to a remote PC: Operator lockout After 3 consecutive failed log-in attempts, the Operator is temporarily blocked (for 30 seconds) from connection attempts. After the lockout period expires, the Operator will be able to connect again. Protection of customer computer and data An essential part of Ammyy Admin security is its permission-based access control model for protecting access to the customer's computer and the data contained therein. Before Operator gains access to remote PC, Client sets permissions for this particular Operator. For example, one can limit Operator access to "view screen only", or block file manager or grant full access to the PC. Secure unattended administration The unattended server administration feature allows connection to a remote PC, even if there is no person at Client PC to participate in Ammyy Admin session. Unattended administration can be set by installing Ammyy Admin as a service on Client PC and adding access permissions for certain Operators IDs. A more detailed guide to unattended administration can be found here http://www.ammyy.com/en/admin_unattended.html Communications security features Communication between participants in Ammyy Admin session occurs via an overlay multicast networking stack that logically sits on top of the conventional TCP/IP stack within each user's computer. The communications architecture is summarized in the figure below. Ammyy Admin session participants ("endpoints") communicate with Ammyy Inc. infrastructure communication servers and gateways using outbound TCP connections on ports 80, 443 or 8080, depending on availability. Ammyy Admin allows communication through HTTPs Proxy with SSL encryption if necessary. Because Ammyy Admin is a hosted service, participants can be located anywhere on the Internet — at a remote office, at home, at a business centre or connected to another company's network. Communications confidentiality and integrity
Ammyy Admin provides data security measures that address attacks against data integrity and confidentiality. All Ammyy Admin connections are encrypted and access to Client PC is possible only for authorized Operators. Display data, keyboard/mouse control data, transferred files and voice are always exposed in encrypted form. The Ammyy Admin session encryption key is not kept on Ammyy Inc. servers in any form and cannot be discovered or derived by Ammyy Inc. servers or personnel. Thus, breaking into a server cannot reveal the key for any encrypted stream that the intruder may have captured. Encryption
Ammyy Admin data encryption is primarily based on 1024-bit RSA and 256-bit AES standards which are used to protect all communication between session participants. New session keys are generated for each session by endpoints, and are never known to Ammyy Inc. or its systems and communication servers only route encrypted packets and do not have the session encryption key. This technology is based on the same standards as https/SSL and is considered completely safe by today's standards. Code Signature All files of Ammyy Admin are secured using VeriSign code signing technology. This allows you to verify the origin of the executables you have and no one changed them. |
 |
| Privacy Policy Terms and Conditions EULA | Copyright © 2017 Ammyy. All rights reserved. |














 How
Ammyy Admin can be used
How
Ammyy Admin can be used